How to upgrade Paloalto firewall-
Why we need ugradation ---
-->> Bug fixes that are not available in current version
-->> Current version is going to End of Life soon
--->> Patches for security vulnerabilities in PAN-OS
Before starting upgrade, we need to understand a few things --
-->> Before you upgrade, make sure the firewall is running a version of app + threat (content version) that meets the minimum requirement of the new PAN-OS
--->> Recommendation is always run the latest version of content to ensure the most accurate and effective protections are being applied
also make sure you can verify the version with Paloalto Tac, Make sure your hardware is support that particular version that you want to upgrade.
-->> Panorama should be running the same or a later version of a feature release than the firewall
--->> Panorama should also be running the same or later version of a maintenance release than the firewall (up to two maintenance versions is supported
--->> panorama may manage a firewall that is running on a later maintenance release than its own, but more than 2 versions are not recommended (ie. Panorama 8.0.0 can manage firewalls up to 8.0.2)
Please note - Devices are upgraded one major version at a time, HA will remain active and continue to synchronize sessions and no network outage will be seen
Pre-health check --
1- verify the version which you are going to upgrade
2- Please make sure don't upgrade Panorama and Firewall at same time
3- Always schedule change into non-working hours only
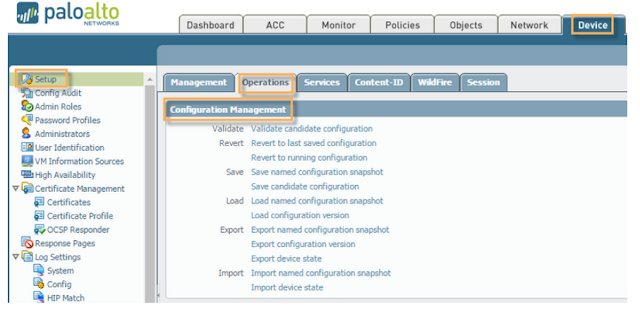
4- Take backup of firewall -
-->> Device > Setup > Operations > Save Named Configuration Snapshot
Please make sure you should create a Tech file also -
Device > Support > Generate Tech Support File
-->>> Disable TCP state checking
-->>> Non-syn TCP reject
--->> Any debug setting if existing (not recommended)
Now you need to download both image like base image and latest image of os.
and upload the base image after reboot the system then go to the latest image.
Note - Latest the PAN-OS upgrade, you may need to upgrade associated software (such as GlobalProtect agent or User-ID agent)
Next step --
Try to arrange one Data center guy who can provide console for any unexcepted error.
Firewall upgrade ----------
if you have the pair in HA(active/passive) then you have to upgrade only to next version of PAN-OS then failover and proceed to upgrade for the second version of PAN-OS. Only upgrade one version at a time
Note - if there is more than 1 version of the difference between the HA pairs then you will run into the “Peer version too old” issue.
-->> Ensure that HA failover is functioning properly
-->> Ensure that the passive firewall is functioning properly and is able to pass traffic without issues
-->> Disable Preemption if enabled.
-->> Disable Preemption on High Availability settings to avoid unexpected failovers.
Disabling preempt configuration change must be committed on both peers. Once completed, re-enabling must be committed on both peers
See below pic to disable preemption-
Steps for upgradation --
Step 1-
Primary firewall, Suspend the Primary firewall to make the Secondary firewall active
-->> CLI: > request high-availability state suspend
After this verify HA connectivity make sure that everyting is working as expected.
Step 2-
-->> Download 8.0.0 (base version)
-->> Download and install the latest preferred 8.0.x maintenance release and reboot to complete the upgrade
-->> On the Primary firewall, verify auto commit completes successfully (FIN OK) by running the command before proceeding to the next step: > show jobs all
--->> Run the following command to make Primary firewall functional again: > request high-availability state functional
Now primary firewall is upgraded, next start on secondary box, so first shift traffic from Secondary to Primary , as use same command suspend state
Use same step as the primary one for upgradation.
Post upgradation verification -
-->> Make sure that both Primary and Secondary firewalls are both running the new software, it is a good idea to test failover functionality again
-->> Run the following comma to suspend Primary firewall to fail traffic to the Secondary firewall "request high-availability state suspend"
-->> verify all applications are working
Run "request high-availability state functional" on both device in HA and verify the config
Note - After upgrade Enable preemption if it was disabled due to upgrade
If you faced any issue need to connect with paloalto TAC or you should downgrade your upgrade.











No comments