How to configure Site to Site VPN in checkpoint
How to configure Site to Site VPN in checkpoint -
There are below steps to configure Site to Site VPN into Checkpoint -
We can follow the Below Step --
-->> Enable IPSec VPN Blade on Gateway
-->> Define ID Domain
-->> Create Community
-->> Add Rule
-->> Create Community--
1- Go into SmartConsole > tab, in the area, click
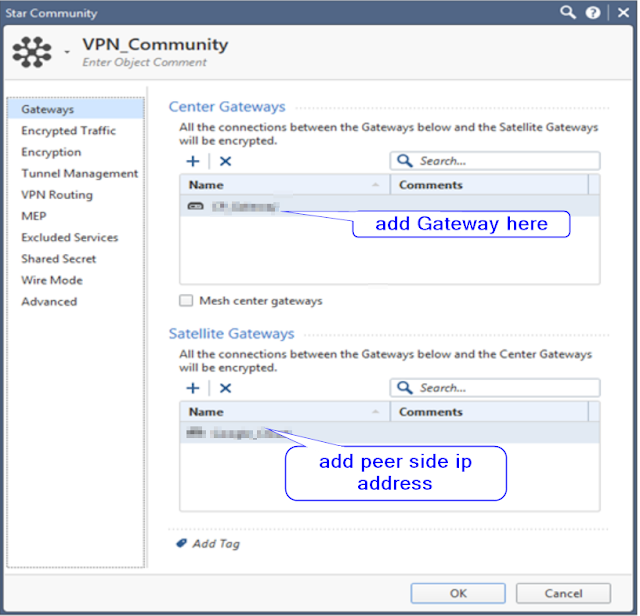
2- New icon and select Star Community and create new Star Community and Enter name of Star community
3 - In the Center Gateways area, click the plus icon to add one or more gateways to be in the center of the community
4 - In the Satellite Gateways area, click the plus icon to add peer side external ip address
Go into the Advanced menu and set Renegotiate every
1- IKE phase 1 - Renegotiate every: 1440
2- IPSEC Phase 2 - Renegotiate every: 3600
--->> Add rule <<---
-->> Define ID Domain -->>
Browse to the object list and click > or to define a new group of machines or networks.
--->> Routing <<--
By default, IPsec VPN uses the main IPv4 Address, defined in the General Properties page of the Gateway, for the VPN tunnel connection
please note - if you want to use this IP address for the VPN communication, and it is an external interface, you do not need additional routing
We can configure the Same thing on the Remote side box and make sure Phase 1 and Phase 2 parameter must Identical both side.
Check the VPN status --
1- vpn tu launches the TunnelUtil tool, which is used to control VPN tunnels
run #vpn tu and see below output
********** Select Option **********
(1) List all IKE SAs
(2) List all IPsec SAs
(3) List all IKE SAs for a given peer (GW) or user (Client)
(4) List all IPsec SAs for a given peer (GW) or user (Client)
(5) Delete all IPsec SAs for a given peer (GW)
(6) Delete all IPsec SAs for a given User (Client)
(7) Delete all IPsec+IKE SAs for a given peer (GW)
(8) Delete all IPsec+IKE SAs for a given User (Client)
(9) Delete all IPsec SAs for ALL peers and users
(0) Delete all IPsec+IKE SAs for ALL peers and users
(Q) Quit
3- vpn shell /tunnels/delete/IKE/peer/[peer ip] - delete IKE SA
4- vpn shell /tunnels/delete/IPsec/peer/[peer ip] - delete Phase 2 SA
5- vpn shell /show/tunnels/ike/peer/[peer ip] - show IKE SA
6- vpn shell /show/tunnels/ipsec/peer/[peer ip] - show IPSEC
Use Debug Command --
2- vpn debug on|off -- Debug VPN into $FWDIR/log/vpnd.elg. Analyze vpnd.elg with the IKEView tool
3- vpn debug trunc -- Truncate and stamp logs, enable IKE & VPN debug
4- vpn drv stat -- Show status of VPN-1 kernel module





















No comments