How to Configure IPSec VPN on Palo Alto Firewall
How to Configure IPSec VPN on Palo Alto Firewall
We need to configure below steps to configure S2S vpn into Paloalto
-->> Tunnel Zone
-->> Tunnel Interface
-->> IKE Crypto (phase 1)
-->> IPSec Crypto (phase 2)
-->> IKE Gateway
-->> IPSec Tunnel
-->> Routes
-->> Security Policy
1- Inside- For internal traffic
2- Outside - this connect to Internet
3- VPN - this zone use for VPN tunnel
---->> Configure Tunnel Interface <<---
1- Login into Webgui -->> Go into Network Tab-->> Tunnel Interface
Interface Name: tunnel.12
Virtual Router: MY-VR
Security Zone: VPN
IPv4: 192.168.1./30
Virtual Router: MY-VR
Security Zone: VPN
IPv4: 192.168.1./30
---->> IKE Crypto (phase 1) <<---
1- Go to Network >> Network Profile >> IKE Crypto and click Add
Name: Test-IKE-CRYPTO
DH Group: group5
Authentication: sha256
Encryption: aes-192-cbc
Timers (Key Lifetime): 50,000 seconds
DH Group: group5
Authentication: sha256
Encryption: aes-192-cbc
Timers (Key Lifetime): 50,000 seconds
--->> IPSec Crypto (phase 2)<<-----
1- Go to Network >> Network Profile >> IPSec Crypto and click Add.
Name: Test-IPSEC-CRYPTO
Encryption: aes-256-cbc
Authentication: sha1
DH Group: group2
Lifetime: 10,000 seconds
Encryption: aes-256-cbc
Authentication: sha1
DH Group: group2
Lifetime: 10,000 seconds
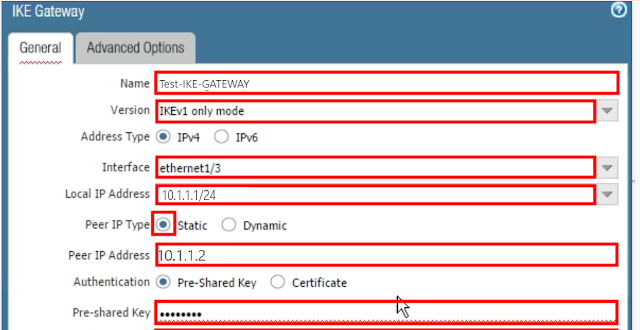
----->>> IKE Gateway<<<-----
1- Go to Network >> Network Profile >> IKE Gateway and click Add
Name: Test-IKE-GATEWAY
Version: IKEv1
Interface: ethernet1/1 (IPSec interface)
Local IP Address: 10.1.1.1/24
Peer IP Address Type: IP
Peer Address: 10.1.1.2
Authentication: Pre-Shared Key
Pre-shared Key: "Test@123"
Version: IKEv1
Interface: ethernet1/1 (IPSec interface)
Local IP Address: 10.1.1.1/24
Peer IP Address Type: IP
Peer Address: 10.1.1.2
Authentication: Pre-Shared Key
Pre-shared Key: "Test@123"
Now click on Advanced Tab and select our IKE crypto profile.
--->>>IPSec Tunnel---->>
1- Go to Network >> IPSec Tunnels and click Add-
Name: TEST-IPSEC
Tunnel Interface: tunnel.12
IKE Gateway: Test-IKE-GATEWAY
IPSec Crypto Profile: Test-IPSEC-CRYPTO
Tunnel Interface: tunnel.12
IKE Gateway: Test-IKE-GATEWAY
IPSec Crypto Profile: Test-IPSEC-CRYPTO
In this profile, we can call our both profile IKE and IPSEC on that and include the Tunel group which we created Tunnel .12
In Proxy id , we only allowed interested traffic on that like LAN IPs
---->>> Routes<<-----
Add routes to reach PA-A to PA-B and vise-versa. Below are the route from PA-A to PA-B, where the gateway is IPSec peer IP, which is 192.168.1.1
--->> Security Policy<<---
-->> We can use two policies for this Site to site VPN
1- IPSec
2- For LAN to LAN communication between peer
-->> IPSec
Source Zone: Outside
Destination Zone: Outside
Application: ike, ipsec-esp
-->> For LAN to LAN communication between peer
Source Zone: LAN & VPN
Source IP: 172.16.0.0/24 & 10.10.10.0/24
Destination Zone: LAN & VPN
Destination IP: 172.16.0.0/24 & 10.10.10.0/24
Application: any
-->> check Logs <<--
1 - Go into Monitor -->> logs -->> system
# show vpn ike-sa
#show vpn flow name "tunnel name"
# show running tunnel flow
Please command if you still face any issue.
Thanks
























No comments