How to configure Site to site vpn between azure to on premise
Step by Step How to Configure Site-to-Site VPN Microsoft Azure to FortiGate
How to configure site-to-site VPN between Azure cloud and Fortigate firewall, we use below point.
- Creating the Microsoft Azure virtual network
- Creating the Microsoft Azure virtual network gateway
- Creating the Microsoft Azure Local network gateway
- Creating the VPN Connection
- Configuring the FortiGate tunnel
- Creating the FortiGate firewall addresses
- Creating the FortiGate firewall policies
- Connectivity Test
Create the Virtual Networks -
we can follow below steps -
1- create virtual network
- Subscription: Select your active subscription.
- Resource group: Select an existing resource group or we can create a new resource group.
- Name: We have to provide a meaningful name for the virtual network.
- Region: Select the nearest Region.
Now review request and create virtaul network
Go to resource button to navigate to the virtual network interface.
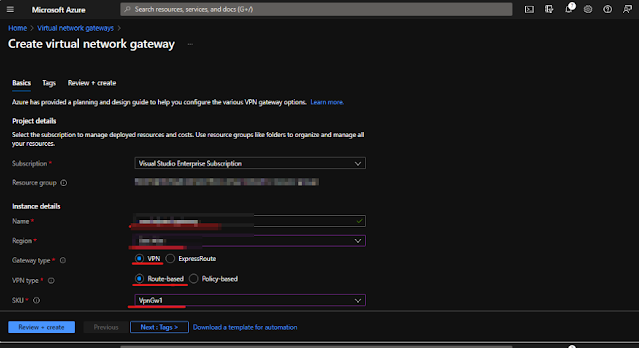
Now Virtual Network Gateway --
-->> Search Virtual network gateway and click on the search result Virtual network gateway
-->> Basics tab and then provide the below details as your wish ---
- Name: We have to provide a name that matches the name of our new virtual network.
- Gateway type: Select VPN.
- VPN type: Select Route-based VPN.
- SKU: Select Basic, as it fits the requirements of most SMBs (Server Message Blocks).
- Virtual network: Choose the Virtual Network that we created.
- Public IP address: Create a new public IP address, give it a meaningful name
Now validate the process and create -
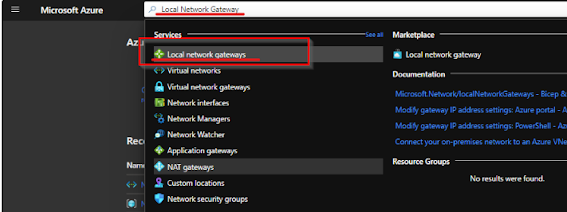
We should create another interface to represent Our local on-premises network , now seach Local Network Gateway
Create a Site-to-Site VPN between Azure to FortiGate
Virtual network gateways interface then click on the Connections tab
- Name: Provide a name related to the Azure Virtual network that you are creating.
- Connection type: From the drop-down, select Site-to-Site (IPSec).
- Local network gateway: Select the Local network gateway that we created.
- Shared key (PSK): Provide a complex string and save it securely. You must provide this key on your on-premises firewall.
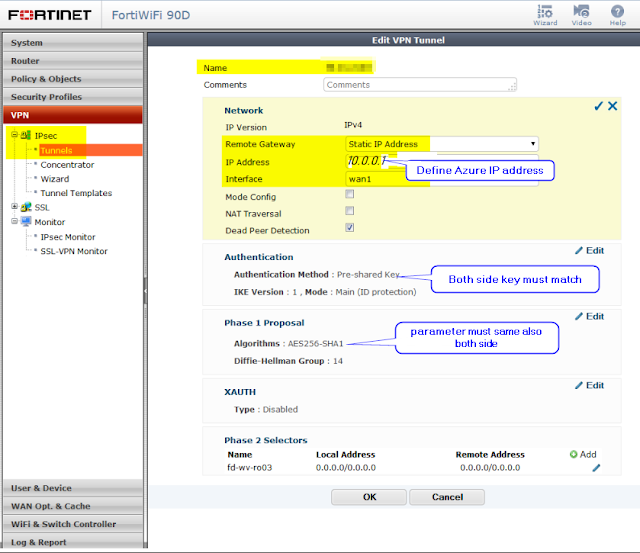
Now we can configure Fortigate Firewall
On-Prem FortiGate Firewall configuration ---------- -------------------
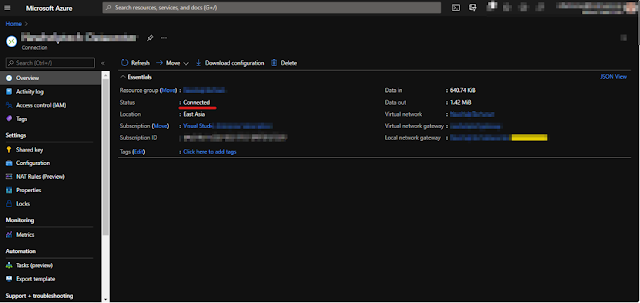
now check traffic and status on Azure and try to ping Azure ip from ONpremise


























No comments